Collaborative Research: SWIFT: Coexistence and Interference Mitigation in the Mid-Band Spectrum: Analysis, Protocol Design, and Experimentation
Rapid proliferation of mobile technologies, manifested by a boom in smart phones and mobile video, along with the emergence of new verticals such as industrial IoT and autonomous vehicles, placed high demand on the communications infrastructure and motivated the introduction of 5G cellular systems. Compared to its 4G/LTE predecessor, 5G systems promise to deliver orders of magnitude higher data rates, significantly lower end-to-end latency, much denser connectivity, seamless coverage, high reliability, and longer battery lifetime. Facilitating these performance gains are advances on multiple fronts, most notably access to new swaths of the radio frequency (RF) spectrum. In addition to opening new spectrum above 24 GHz for 5G systems, the FCC and other regulatory bodies also created new opportunities at mid-bands below 7 GHz (“beachfront spectrum”). These bands exhibit favorable propagation characteristics that enable wide-area coverage at high data rates.
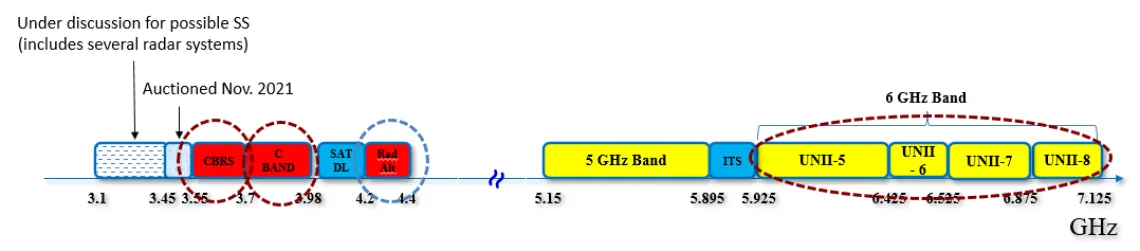
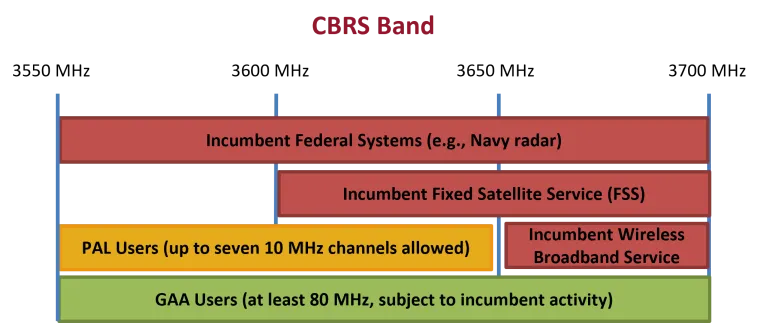
This project focuses on addressing coexistence challenges over three recently available mid-bands: the C-band (3.7-3.98 GHz), the CBRS band (3.55-3.7 GHz), and the recently unlicensed 6 GHz bands (5.925-7.125 GHz). These bands have been only recently allocated for commercial wireless systems, which will have to coexist on these bands with a wide variety of incumbents, including Navy radar in 3.55–3.7 GHz CBRS band, point-to-point microwave links and passive radioastronomy receivers (e.g., the Methanol line) in the 6 GHz bands, and adjacent radar altimeters in the 4.2–4.4 GHz band. The proposed research agenda includes three thrusts. In the first thrust, the PIs will focus on coexistence and interference mitigation in the C-band. Despite extensive media coverage of the potential of 5G interference onto radar altimeters, there is a lack of rigorous, unbiased analyses and measurement of such interference in realistic operational scenarios. The PIs will accurately characterize C-band interference and establish the conditions under which it may occur. Novel machine learning (ML) techniques will be developed for real-time detection of interference and mitigation of its impact by adapting the 5G transmission parameters. The second thrust focuses on coexistence and interference mitigation in the CBRS band, particularly secondary coexistence between Tier 3 (GAA) users, which is quickly emerging as a bottleneck to efficient use of the band. Protocol-based and ML-based solutions will be explored. The third thrust focuses on coexistence in the unlicensed 6 GHz bands, where ML-based protocol classification designs will be explored to allow a given device to detect the underlying protocols of other devices and adapt its parameters accordingly. The proposed solutions will be evaluated via simulations and field measurements. These solutions are expected to have broader applicability beyond the specific studied bands. Research outcomes from this project will be shared with industry and will be provided to the FCC as case studies to facilitate subsequent policy making in other bands. The proposed research will be fully integrated into the educational plan by incorporating its outcomes in newly designed and existing courses as well as training undergraduate and graduate students via mentoring, participation in test-bed development, and special projects. The project contains a detailed plan to broaden participation of underrepresented groups via various channels established in the past years.
Secure and Verifiable Cloud Storage
Overview: Cloud computing promises ubiquitous, on-demand access to an expandable pool of computing resources, including storage, computation, and software services. However, the risk of losing outsourced data due to failures or security breaches exposes cloud users to grave legal, financial, and business liabilities. In this project, we aim at developing provably secure, privacy-preserving methods for verifying the fault-tolerant storage of voluminous data at remote repositories. We focus on the Infrastructure-as-a-Service (IaaS) model, and in particular, a typical remote storage scenario in which the cloud storage provider (CSP) contractually agrees to maintain a large repository with a certain degree of reliability, outlined in a Service Level Agreement (SLA). This project focuses on a comprehensive research agenda at the cross-paths of security, error-correction coding, and networking that aims at achieving verifiability, privacy, and resource efficiency of remote reliable storage at both the logical level (storage of data and redundancy) and physical level (distribution across physical devices and locations).
A Stochastic Resource Allocation and Task Assignment Framework for Mobile Edge Computing
Mobile edge computing (MEC) is an emerging platform for supporting rapidly growing low-latency mobile applications and Internet of Things (IoT) systems. It involves deploying nodes with computing, storage, and communication capabilities at the edge of mobile networks and utilizing client mobile devices for computing and data processing services near end users. This project addresses the challenges of resource allocation and task assignment in MEC systems, enabling horizontal and vertical cooperation among edge nodes, remote cloud data centers, and mobile users for performance optimization of multiple services with different quality of service (QoS) requirements. Specifically, a stochastic framework for cooperative resource allocation and task assignment in MEC systems is designed using deep learning, stochastic game, and optimization techniques.
Our research agenda includes but not limited to following tasks:
- Centralized and distributed algorithms for orchestrating computational tasks in MEC Systems
- Lightweight heuristic algorithms for orchestrating computational tasks
- Latency prediction for delay-sensitive V2X applications in mobile cloud/edge computing systems
- Network slicing and resource allocation schemes for sharing a virtualized heterogeneous MEC network infrastructure
- Proof-of-concept prototyping the algorithms developed under this project
Protocols, Adaptation, and Spectrum Allocation for 5G Millimeter-wave Systems
Fifth Generation (5G) cellular systems are being designed to communicate over both sub-6 GHz as well as millimeter-wave (mmWave) bands. mmWave spectrum offers abundant bandwidth, which will be needed to support multi-Gbps transmission speeds per user, not to mention the stringent latency, connectivity, and reliability requirements associated with some 5G use cases. Despite this abundant capacity, RF communications at mmWave frequencies can be quite challenging, due to high propagation losses, poor penetration, blockage, rain sensitivity, etc. At the same time, due to the smaller wavelengths, phased antenna arrays with tens or even hundreds of elements can be packed into a single device. With proper processing of signals fed into these antennas, highly directional transmissions can be achieved using electronically steerable antennas and/or digital beamforming.
Our research agenda focuses on the following themes:
- Fast Network Discovery and Tracking for 5G mmWave cellular systems
- Optimization and User-dependent Adaptation of Beamwidth
- Blockage-resilient Directional Communications
- mmWave Channel Characterization
- Sharing and Dynamic Allocation of mmWave Spectrum
Machine Learning for Intelligent and Agile Wireless Communications
Classical, model-based techniques for resource management and coordination in wireless networks often rely on a priori assumptions that are too idealized for real deployment scenarios. These techniques generally fail to capture the broad range of parameters and channel access controls that impact network performance, especially in situations involving coexistence of heterogeneous technologies on a shared spectrum. Machine learning (ML) techniques, on the other hand, enable the adaptation of a wide range of control parameters (features), with no or minimal assumptions on the underlying channel and network dynamics. ML techniques have recently been studied and applied to numerous wireless systems, from sensor networks to 5G millimeter-wave (mmWave) transmissions. The stringent quality of service (QoS) requirements associated with certain use cases of 5G+ wireless systems (e.g., ultra-reliable low-latency communications and eMBB) along with the integration of edge computing (MEC) platforms into these systems have triggered intensive research on the use of ML for wireless communications.
The overarching goal of our research endeavor is to explore ML techniques for fast protocol adaptation, resource allocation, and spectrum sharing in both mid-band (sub-6 GHz) as well as high-band (mmWave) wireless systems. Our research strategy is to combine model-free ML tools (“black box”) with robust and highly generic modeling assumptions (hence, a “grey box” overall design) so as to achieve computationally efficient real-time adaptation of complex wireless networks under limited information. We leverage the flexibility of ML techniques to incorporate a large set of diverse but observable inputs into the learning engine. In contrast to existing state-of-the-art ML-based techniques that over-emphasize performance over complexity, our proposed designs target fast/real-time adaptation. Specific themes in our ML-based research agenda include, but are not limited to:
- User Tracking and Link/Beamwidth Adaptation in 5G mmWave Systems
- Interference Mitigation in Contention-based Wireless Networks
- Intelligent Scheduling of Time/Frequency Resources in OFDMA Wireless Systems
- Misbehavior Detection and Protocol Compliance for Unlicensed Wireless Networks
- Lightweight Machine Learning for Efficient Frequency-Offset-Aware Demodulation
Erasing Wireless Fingerprints: PHY-layer Countermeasures for Secure Communications
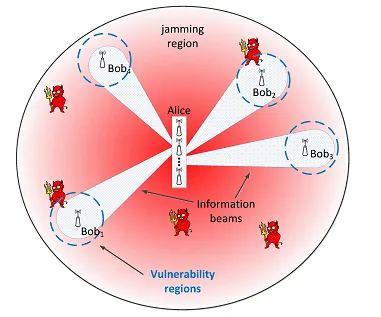
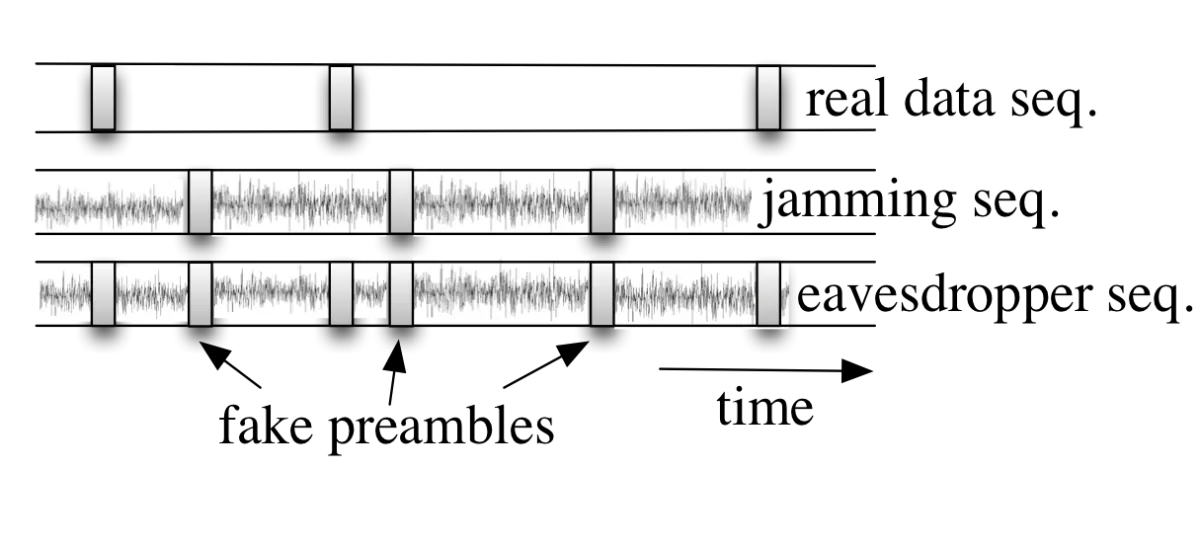
The open nature of the wireless medium leaves it exposed to adversarial eavesdroppers. Using commodity radio hardware, unauthorized adversaries can easily intercept packet transmissions. Although encryption can be applied to ensure information secrecy, eavesdroppers can still perform low-level RF and traffic analysis, and capture with different degrees of certainty several communication attributes, such as the packet size, its duration, inter-packet times, traffic directionality, channel state information, etc. Through knowledge of the protocol semantics, these attributes can be correlated to create transmission fingerprints, from which an adversary can derive a wealth of contextual information, including the relative significance and locations of the communicating parties, their mobility patterns, the applications they run, their visited sites, etc. Contextual information can be subsequently used to launch sophisticated attacks (e.g., selective jamming/dropping, targeted node compromise, intelligent DoS attacks, etc.). State-of-the-art privacy research focuses on the leakage of high-layer attributes, typically captured from unencrypted headers. In fact, most efforts in this domain deal with demonstrating the feasibility of privacy attacks, and less with providing remedies. Countermeasures are often limited to specific "point" attacks, without addressing their root cause, i.e., the exposure of transmission signatures. In this project, we aim at advancing the state-of the-art on signature-free secure wireless communications. Our techniques are meant to counter different time scales of eavesdropping. For short-term eavesdropping, we are developing novel PHY-layer techniques for concealing transmission attributes. These techniques exploit advances in MIMO and self-interference suppression to provide integrated transmitter/receiver friendly jamming, with the goal of preventing eavesdropping irrespective of the eavesdropper's location. Novel digital/analog signal combining schemes are also used to obfuscate additional fingerprints. For longer time-scale and/or colluding eavesdroppers, we are developing randomization techniques that aim at countering traffic and frequency inference attacks facilitated by long-term monitoring of transmission activities over several links.
Reconfigurable Antennas and Optimized Multi-channel MIMO Designs for DSA Systems with a Broad Frequency Coverage
Over the last two decades, dynamic and opportunistic spectrum access (DSA/OSA) has been advocated as a new paradigm for improving the utilization of the licensed spectrum below 6 GHz. Spectrum regulators (e.g., FCC, NTIA, etc.) embarked on numerous initiatives that aim at identifying underutilized portions of the licensed spectrum and exploring new models for spectrum sharing among different types of users. These initiatives include the FCC's ruling on TV broadcast channels in the 54 to 698 MHz range (so-called TV whitespaces or TVWS), the FCC's Notice of Proposed Rule Making (NPRM) on the 3.55-3.65 GHz radar band (which lays the groundwork for coexistence between small-cell LTE systems, military radar, and other incumbent systems), and others. Similar initiatives are taking place in other regions of the world, such as the European Union (EU)'s efforts to explore the 2.2-2.3 GHz band for spectrum sharing between aeronautical telemetry radar and small-cell LTE systems. The role of radio spectrum as a critical economic growth engine was highlighted in the 2012 President's Council of Advisors on Science and Technology (PCAST) report, which recommended creating "the first shared-use spectrum superhighways."
Yet, despite this strong push, commercial DSA wireless services have not proliferated. This is in part due to the limited availability of TVWS in urban areas and, more critically, their spatial non-uniformity across the Continental US. Broadcast TV stations in the US are licensed to operate over 6 MHz wide (NTSC) channels that fall into four noncontiguous segments of the spectrum (52-72 MHz, 76-88 MHz, 174-216 MHz, and 470-698 MHz). In a given urban location, the number of TV channels available for opportunistic access can be as low as 2 to 4, after accounting for FCC protection rules (e.g., power masks, adjacent-channel interference, etc.) and "TV pollution" zones, i.e., areas where TV signals are not decodable but are strong enough to disrupt secondary (opportunistic) transmissions. Not only that these channels are too few, but they often have to be shared by several secondary users (SUs), raising the prospects of SU-SU interference. The non-contiguity of available TV channels further complicates matters, as complex carrier/channel aggregation techniques must now be used over a given link to achieve WiFi-comparable channel widths (e.g., 20 MHz and higher).
The overarching goal of the underlying project is to enable DSA operation over a large swath of the opportunistic spectrum below 6 GHz, including the UHF portion of TVWS (470-698 MHz segment), the 3.5 GHz radar band, as well as other bands in the 1 to 4.4 GHz range that may later become candidates for DSA. By aggregating different (not necessarily contiguous) portions of the RF spectrum at the same wireless device, we anticipate that variations in white/grey spaces can be significantly reduced, allowing for sustained DSA operation over a large geographical area. Enabling such operation while maintaining high link throughput requires advances in the following areas:
- Electrically small tunable antennas that allow for dynamic access to narrowband (e.g., 6 MHz) channels, but yet support a broad frequency range from 470 MHz to 4.4 GHz.
- Channel/carrier aggregation techniques for noncontiguous narrowband channels.
- Multi-channel MIMO functionality that allows a given secondary link to boost its throughput (via spatial multiplexing gain) and, simultaneously, minimize interference onto other coexisting systems (via MIMO precoding techniques).
The first capability is intended to beef up the agility of the secondary radio, allowing it (for example) to switch between TVWS and the radar band, on demand. The last two capabilities are intended to significantly increase the per-link throughput and reduce SU-SU interference. Through novel advances in the above areas, we plan to design, implement, and experimentally evaluate a multi-channel 2-by-2 MIMO system for DSA with a broad RF coverage. Our research agenda involves optimizations at both the signal level (via MIMO precoders) as well as the antenna level (via highly tunable small form-factor reconfigurable antennas).
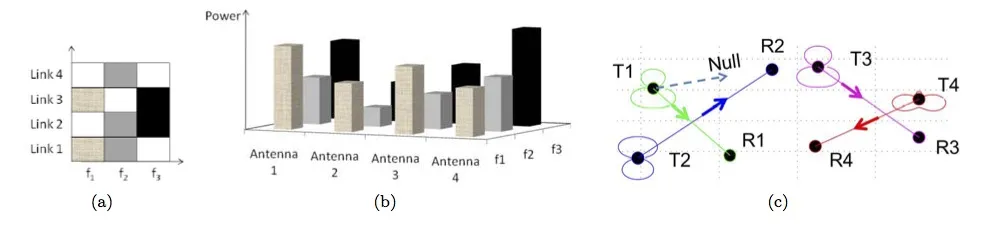
Control dimensions in a CMIMO WLAN: (a) Frequency allocation among multiple links, (b) power allocation over frequencies and antennas, and (c) beamforming-based interference suppression. The example shows a WLAN of 4 links, 2 antennas/node, and 3 channels.
Secure Spectrum Sharing and Coexistence of Heterogeneous Wireless Systems
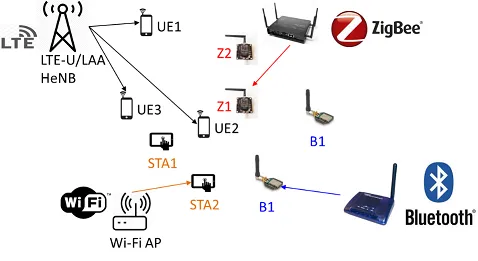
The dramatic growth in demand for wireless services has fueled severe spectrum shortage, especially in the unlicensed bands below 6 GHz. The regulatory approach for meeting this galloping demand is to allow coexistence of competing technologies (LTE LAA, 5G NR-U, Wi-Fi, C-V2X/DSRC, radar, etc.) over shared spectrum. Although the concept of spectrum sharing in itself is not new, the heterogeneity of the coexisting systems, their scale, and lack of explicit coordination mechanisms among these systems pose novel challenges for secure, efficient, and fair resource allocation. Whereas some recent efforts have tried to address the coexistence of specific technologies, a comprehensive and general approach to securely and efficiently coordinate spectrum access for heterogeneous systems remains elusive. By facilitating fair and secure coexistence of heterogeneous wireless systems, this project directly addresses the spectrum scarcity challenge. The outcomes of this project will benefit many industry verticals, including intelligent transportation, manufacturing, agriculture, critical national infrastructure, telecommunications, and others. Moreover, the expected results will advance knowledge in a number of scientific fields including security, privacy, and communication theory. Training opportunities for future wireless and security experts are also provided.
In this project, we focus on addressing some of these challenges and developing potential solutions. We investigate how fairness and spectral efficiency tradeoffs are to be optimized. We also address the cross-technology detection in heterogeneous networks, and discuss what strategies coexisting systems should adopt.
Full-duplex Wireless Systems
Common handheld wireless radios operate in half-duplex (HD) mode, with one transceiver alternating between transmission and reception. Full-duplex (FD) operation in which a device is capable of simultaneous transmission and reception (STAR) can be achieved by employing multiple transceivers at the same device or (more recently) through orthogonal frequency division multiple access (OFDMA) technology. In both cases, however, STAR is performed over different transmit and receive channels (henceforth called STAR-D capability). Sufficient separation (i.e., guard bands) is needed between the transmit and receive channels to prevent side-lobe interference and spectrum leakage from corrupting the received signal. Until recently, performing STAR over the same channel (a mode that we refer to as STAR-S) was deemed impossible due to strong self-interference. This common belief was recently challenged by several research groups, which have successfully demonstrated the possibility of FD communications using a combination of self-interference suppression (SIS) techniques, including RF analog cancellation, digital baseband interference cancellation, circulators, phase shifters, etc. In fact, it has been shown that a node's own transmission can be suppressed by 73 to 110 dB (noise floor), depending on the underlying SIS schemes. Such a level of SIS has significant ramifications on network protocols, which are often designed with the assumption of HD operation. In this project, we aim at exploiting SIS capabilities in designing efficient protocols for wireless networks. Two main thrusts are being pursued:
- Exploiting SIS in Dynamic Spectrum Access Systems
- Designing Adaptive SIS-aware Multi-channel MAC Protocols for OFDMA-based Wireless Networks
- Studying the Feasibility of Full-duplex Communications from Network's Perspective
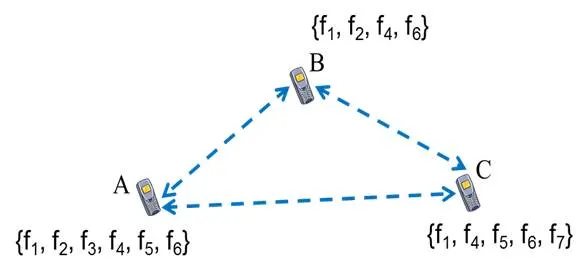
Rendezvous Protocols for Spectrum-agile Wireless Networks
Establishing communications in a multi-channel wireless network requires the communicating devices to "rendezvous" on a common channel before carrying out normal data transmissions. The rendezvous process enables the exchange and negotiation of critical information, including transmission parameters, connectivity and topological changes, etc. This process takes place at the time a new session is established and following the loss of connectivity between the transmitter and receiver (e.g., due to jamming and/or channel fading). Clock drifts make it difficult for the communicating parties to maintain a common time reference, so the rendezvous process must be robust to misalignment and lack of tight synchronization. Moreover, in a dynamic spectrum access (DSA) environment, rendezvousing may need to be conducted under a heterogeneous opportunistic spectrum setting, i.e., the set of idle channels are generally different for different nodes. This heterogeneity is caused by spatiotemporal variations in spectrum availability as well as interference/jamming conditions. In this project, we are developing novel quorum-based frequency hopping (FH) schemes for unicast and multicast rendezvous in wireless networks. The quorum approach makes it possible to come up with more structured (less random) FH sequences, hence increasing the likelihood of overlap (rendezvous) between two or more nodes. At the same time, this structured approach makes devices inherently vulnerable to "insider attacks," i.e., attacks by compromised nodes that exploit knowledge of the underlying quorum system to prevent the rendezvous process for succeeding. Our research deals with both the performance (speed of rendezvous) as well as security (vulnerability to adversarial attacks) issues of quorum-based FH rendezvous designs, under various spectrum and adversarial settings.
Adaptation, optimization, and security of Wi-Fi networks
The wide deployment of Wi-Fi serves for smart homes, intelligent transport systems (ITS), healthcare, and so on. Such ubiquitous deployment raises coverage, capacity, efficiency, and security concerns about Wi-Fi networks. Though the continuous evolvement of Wi-Fi has addressed above concerns to certain extent, there are some remaining spots that have not been well tackled. Firstly, adaptation of certain Wi-Fi protocols is necessary to support user-defined functionality, asymmetric full-duplex communications, and opportunistic transmissions. Moreover, channel access fairness should be regulated to guarantee the overall throughput as the spectrum is too limited for dense deployment and heavy traffic. Finally, Wi-Fi networks operating on unlicensed band are exposed to various Physical-layer and medium access control (MAC) layer attacks which motivates us to develop defense mechanisms.
Our research agenda includes but not limited to following tasks:
- Adaptive Preamble Embedding for User-defined Functionalities
- Attacks and Countermeasures against the Wi-Fi Networks
- Mechanisms for Fair Channel Access and Aggressive Behavior Detection
- Provisioning QoS in Wi-Fi Systems with Asymmetric Full-Duplex Communications
- Autonomous and Scheduled Transmissions in Wi-Fi 6 (802.11ax) Systems
- Throughput-Fairness Tradeoff with Adaptive Clear Channel Assessment
- Adaptive Cross-Layer Protocol Design for Opportunistic WLANs over TVWS
