Erasing Wireless Fingerprints: PHY-layer Countermeasures for Secure Communications
The open nature of the wireless medium leaves it exposed to adversarial eavesdroppers. Using commodity radio hardware, unauthorized adversaries can easily intercept packet transmissions. Although encryption can be applied to ensure information secrecy, eavesdroppers can still perform low-level RF and traffic analysis, and capture with different degrees of certainty several communication attributes, such as the packet size, its duration, inter-packet times, traffic directionality, channel state information, etc. Through knowledge of the protocol functionality, these attributes can be correlated to create transmission “fingerprints”, from which an adversary can derive a wealth of contextual information, including the relative significance and locations of the communicating parties, their mobility patterns, the applications they run, their visited web-sites, etc. Contextual information can subsequently be used to launch sophisticated attacks (e.g., selective jamming/dropping, targeted node compromise, intelligent DoS attacks, etc.). State-of-the-art privacy research focuses on the leakage of high-layer attributes, typically captured from unencrypted headers. In fact, most efforts in this domain deal with demonstrating the feasibility of privacy attacks, and less with providing remedies. Countermeasures are often limited to specific “point” attacks, without addressing their root cause, i.e., the exposure of transmission signatures.
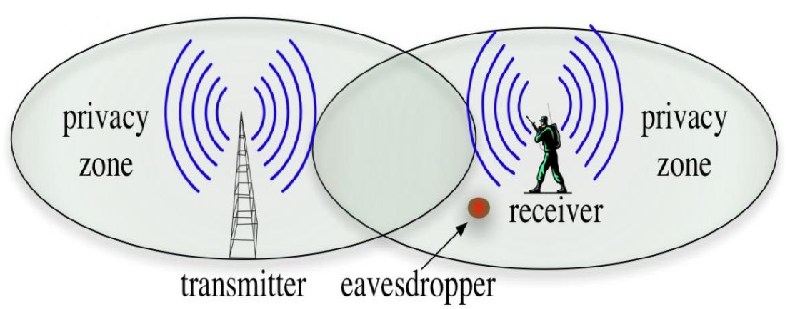
Figure 1 - (a) Transmitter injects artificial noise to create a privacy zone. A vulnerability zone is created around the receiver. An eavesdropper in close proximity to the receiver can decode transmitted packets. (b) proposed system: both the transmitter and the receiver inject artificial noise in order to extend the privacy zone to any possible eavesdropper location. The receiver uses self-interference suppression techniques to decode the packets sent by the transmitter.
In this project, we aim at advancing the state-of the-art on signature-free secure wireless communications. Our techniques are meant to counter different time scales of eavesdropping. For short-term eavesdropping, we are developing novel PHY-layer techniques for concealing transmission attributes. These techniques exploit advances in MIMO and self-interference suppression to provide integrated transmitter/receiver friendly jamming, with the goal of preventing eavesdropping irrespective of the eavesdropper's location. Novel digital/analog signal combining schemes are also used to create to obfuscate additional fingerprints. For longer time-scale and/or colluding eavesdroppers, we are developing randomization techniques that aim at countering traffic and frequency inference attacks facilitated by long-term monitoring of transmission activities over several links.
Related Publications
-
Hanif Rahbari and Marwan Krunz, "Full frame encryption and modulation obfuscation using channel-independent preamble identifier," IEEE Transactions on Information Forensics and Security, vol. 11, issue 12, pp. 2732-2747, Dec. 2016.
-
Hanif Rahbari and Marwan Krunz, "Rolling preambles: Mitigating stealthy FO estimation attacks in OFDM-based 802.11 systems," Proc. of the IEEE CNS 2016 Conference, Oct. 2016.
-
Hanif Rahbari, Marwan Krunz, and Loukas Lazos, "Swift jamming attack on frequency offset estimation: The Achilles' heel of OFDM systems," IEEE Transactions on Mobile Computing (TMC), vol. 15, issue 5, pp. 1264-1278, May 2016.
-
Hanif Rahbari and Marwan Krunz, "Secrecy beyond encryption: Obfuscating transmission signatures in wireless communications," IEEE Communications Magazine -Feature Topic on Wireless Physical Layer Security, vol. 53, issue 12, pp. 54-60, Dec. 2015.
-
Rashad Eletreby, Hanif Rahbari, and Marwan Krunz, "Supporting PHY-layer security in multilink wireless networks using friendly jamming," Proc. of the IEEE GLOBECOM 2015 Conference, Dec. 2015.
-
Hanif Rahbari and Marwan Krunz, "Friendly CryptoJam: A mechanism for securing physical-layer attributes," Proc. of the ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec 2014), July 2014.
-
Hanif Rahbari, Marwan Krunz, and Loukas Lazos, "Security vulnerability and countermeasures of frequency offset correction in 802.11a systems," Proc. of the IEEE INFOCOM 2014 Conference, Apr. 2014.
Obfuscation Using Tx- and Rx-based Friendly Jamming
In this project, we focus on a single collision domain, e.g., a wireless LAN or an ad hoc network where multiple authorized but potentially interfering flows are transported wirelessly (one hop) in the presence of several eavesdroppers. Different degrees of uncertainty regarding the locations or CSI of eavesdropping devices are considered, ranging from no information to complete information. “Mixed” scenarios, where accurate location information or CSI is available on some of the eavesdroppers, are also considered (e.g., eavesdroppers that later on become active transmitters/jammers may be localized). Our study will be conducted under various eavesdropping capabilities, e.g., size of antenna array at each Eve, her receive-based beamforming capabilities (if any), her reactiveness, the possibility of collusion among multiple Eves, etc.
From a system architecture standpoint, two networking scenarios are considered in this thrust: Multi-user MIMO (MU-MIMO) and peer-to-peer (P2P). Directional multibeam multicast, where the same information packet is to be delivered secretly to several receivers, are also treated as a special case of MU-MIMO. Fundamentally, the MU-MIMO setting lends itself to centralized solutions, executed by the access point (AP) or base station (BS). On the other hand, distributed solutions are needed for the P2P setting. Our methods are intended to complement upperlayer cryptographic solutions, adding an extra layer of protection to data confidentiality. They are particularly attractive from a usability perspective, because they are implemented at lower layers, and thus not susceptible to upper-layer vulnerabilities (e.g., poor choice of passwords, phishing attacks, etc.).
1. PHY-layer Security in Multiuser MIMO Networks
This project is motivated by recent studies that showed the vulnerability of the intended receiver to adversaries in its proximity. In particular, when the eavesdropper’s channel is highly correlated with that of a legitimate receiver, MIMO-based nullification of the transmitter’s FJ signal at that receiver, a.k.a. zero-forcing beamforming (ZFBF), extends to nearby eavesdroppers. This increases the signal-to-interference-plus-noise ratio (SINR) at the eavesdroppers (Eves), significantly reducing the secrecy rate. The goal of our work is to provide message confidentiality, independent of the amount of correlations between the channel state information (CSI) at Eve and the intended receiver.
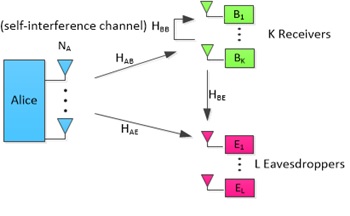
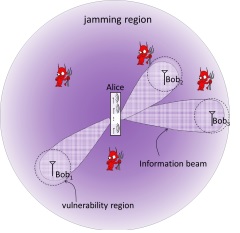
Figure 2 - MU-MISO system model with both TxFJ and RxFJ. Figure 3 - ZFBF of TxFJ signals brings about vulnerability issues around Bobs.
We consider a scenario where the transmitter (Alice) sends K independent confidential messages to K legitimate receivers (Bobs). To achieve message confidentiality, we propose to use receiver-based friendly jamming (RxFJ) along with transmitter-based friendly jamming (TxFJ). This way, Eve’s received signal is degraded even if her CSI is highly correlated with those of Bobs. To remove TxFJ at each Bob, ZFBF is employed by Alice. This technique also provides confidentiality for the information messages (information signals are zero-forced at unintended receivers).
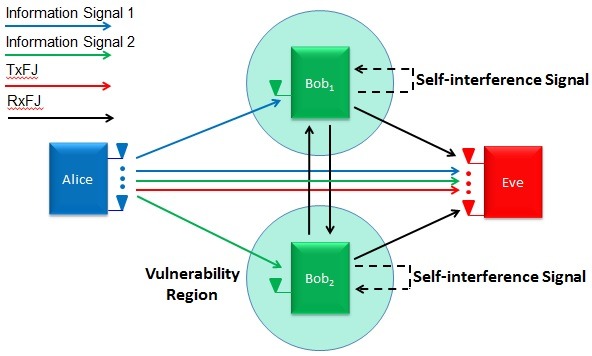
Figure 4 - Cooperative Friendly Jamming: Unintended information and TxFJ signals are nullified at Bobs, whereas Eve receives each one of the information, TxFJ, and RxFJ signals. Bobs are equipped with FD antennas with SIS capabilities.
Achievable Secrecy Sum-rate Maximization: We develop an information-theoretic secrecy precoding scheme for the information signals, and characterize the corresponding secrecy sum-rate. In our scheme, the required amount of randomization to achieve information theoretic security is shared by the codewords intended to Bob and Charlie. Furthermore, these codewords are designed over multiple fading blocks to overcome the limitations of fading and the absence of Eve’s CSI. We formulate an optimization problem to maximize the secrecy sum-rate. The objective is to optimize the power allocation for the two information messages, the TxFJ signal, and the two RxFJ signals (subject to a total power constraint). To investigate the optimal solution for this problem, we further assume that the legitimate links demand a certain SINR to attain a reliable communication, and they cannot communicate if the realized SINR is below this threshold.
Power Minimization: Here, we formulate an optimization problem to minimize the total power consumption for the information, TxFJ, and RxFJ signals, while guaranteeing a certain individual secrecy rate for each Bob with/without eavesdropper’s CSI (ECSI). (In unknown ECSI case, it is assumed that the first- and the second-order statistics of ECSI are known). We exploit the conditions where using RxFJ together with TxFJ has better system performance than using only TxFJ or ZFBF in terms of preventing information leakage to Eves.
The contributions of this project can be summarized as follows:
-
We show that FD capabilities can be exploited in multiuser MISO (multiple-input single-output) networks to provide confidential communications using RxFJ against eavesdroppers, whose channels are correlated with that of legitimate receivers.
-
We investigate the joint power allocation problem for information, TxFJ, and RxFJ signals to satisfy certain secrecy rate requirements, and provide optimal solutions for practical systems.
-
We determine the optimal randomization rates for wiretap coding to confuse the eavesdroppers based on the given requirements (individual secrecy rate requirement if ECSI is known, and secrecy outage probability requirement if only the statistics of ECSI are known).
-
We analyze the effect of different scheduling approaches on the performance of the proposed schemes.
Related Publications
-
Berk Akgun, O. Ozan Koyluoglu, and Marwan Krunz, "Exploiting full-duplex receivers for achieving secret communications in multiuser MISO networks," IEEE Transactions on Communications, vol. 65, issue 2, pp. 956-968, Feb. 2017.
-
Berk Akgun, O. Ozan Koyluoglu, and Marwan Krunz, "Receiver-based friendly jamming with single-antenna full-duplex receivers in a multiuser broadcast channel," Proc. of the IEEE Global Communications Conference (GLOBECOM), San Diego, Dec. 2015.
2. PHY-layer Security in Peer-to-peer (P2P) Networks
The increasing demands for wireless services together with the scarcity of wireless spectrum forces users to share the same band. Sharing the spectrum leads to interference among users. In the jargeon of information theory, such network is known as interference channel. To accommodate simultaneous transmission of several information signals in this network, the signal of each transmitter must be designed to not interfere with other legitimate receivers in the network. To avoid such interference and yet prevent the leakage of the transmission signature, one solution is to exploit MIMO precoding such that the information signal of a link does not interfere with other legitimate links and at the same time kept away from the potential eavesdroppers. This solution, however, is not practical in situations where coordination between legitimate transmitters is challenging (e.g., mobile ad-hoc networks). Therefore, the need for interference management is crucial to guarantee a secure yet non-interfering communications.
The definition of secrecy in interference channel may differ depending on the circumstances of the network. For instance, the links might be interested in the transmission of their neighboring links. Thus, the design must ensure that a given link’s transmission is secured from other links. Such network is referred to as interference channel with confidential messages. Another possibility is when external eavesdroppers exist in the network and the transmissions of network users must be kept secure from eavesdroppers. Such network is referred to as a interference channel with external eavesdroppers or alternatively multi-link wiretap interference channels.
In this project, we aim to study the limits of interference management in interference networks to provide PHY-layer security in its information--theoretic sense. Motivated by the aforementioned challenges, the techniques that we propose can be implemented in distributed fashion with low demand on control message passing (i.e., coordination) between the links. Our methods exploit a manifold of different engineering and mathematical methods/theories such as recent advances in MIMO communications, in-band full-duplex systems, and the well-developed branches of mathematical optimization. Novel methods of distributed beamforming, power control, and signaling are developed in this project to be used in our interference management techniques. Our results are applicable in most of the scenarios where partial knowledge of eavesdroppers' locations/channels are available at the legitimate parties.
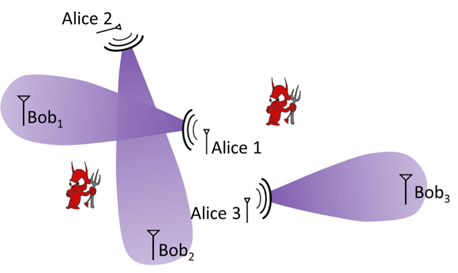
Figure 5 - Multi-link transmissions in an interference network (e.g., peer-to-peer network). The links must use transmission strategies that are secure and non-interfering. Such strategies are required facilitate the need for distributed implementation and low coordination between the legitimate links. The decision parameters include the transmission power, the transmission precoders, the reception decoders, etc. The nearby eavesdroppers could be considered as either external eavesdroppers or the neighboring links interested in the transmission of other links. The interference management techniques must be as close as to being independent of eavesdroppers' locations.
Related Publications
-
Peyman Siyari, Marwan Krunz, and Diep Nguyen, “Distributed power control in single-stream MIMO wiretap interference networks with full-duplex jamming receivers,” in IEEE Transactions on Signal Processing, vol. 67, no. 3, pp. 594-608, Feb. 2019.
-
Peyman Siyari, Marwan Krunz, and Diep Nguyen, “Power games for secure communications in single-stream MIMO interference networks,” IEEE Transactions on Wireless Communications, vol. 17, no. 9, pp. 5759-5773, Sept. 2018.
-
Peyman Siyari, Marwan Krunz, and Diep Nguyen, "Friendly jamming in a MIMO wiretap interference network: A non-convex game approach," IEEE Journal on Selected Areas in Communications, vol. 35, no. 3, pp. 601-614, March 2017.
-
Peyman Siyari, Marwan Krunz, and Diep Nguyen, "Joint transmitter- and receiver-based friendly jamming in a MIMO wiretap interference network," Proc. of the IEEE ICC 2017 Conference - Workshop on Full-Duplex Communications for Future Wireless Networks, Paris, France, May 2017, pp. 1323-1328.
-
Peyman Siyari, Marwan Krunz, and Diep Nguyen, "A game theoretic design of artificial-noise aided transmissions in MIMO wiretap interference network," Proc. of the IEEE GLOBECOM 2016 Conference, Washington, DC, Dec. 2016, pp. 1-6.
-
Peyman Siyari, Diep Nguyen, and Marwan Krunz, "Price-based friendly jamming in a MISO interference wiretap channel," Proc. of the IEEE INFOCOM 2016 Conference, San Francisco, CA, Apr. 2016, pp. 1-9.
